Computer ScienceAn Overview of Essential Security Measures for Competitive OrganizationsTeodor Topalov et. al. - Considering information is the most valuable asset of any organization, information security is one of the most important areas for every business and individual. Looking at the big picture, approximately 86% of all websites had a serious vulnerability in 2015.[1]... Keep Reading »
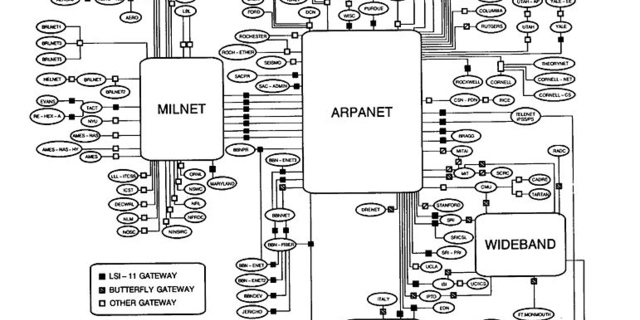
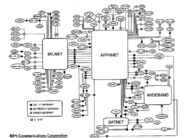
Cracking the Digital Vault: A Study of Cyber EspionageConstantine J. Petallides - Today, we live in the aftermath of the Internet revolution. Humanity has never before been more interconnected or had as much access to the same tools and information. As a driving force behind globalization and modern progress, the Internet enables instant communication... Keep Reading »
A Brief History of CryptographyTony M. Damico - Early cryptography was solely concerned with converting messages into unreadable groups of figures to protect the message’s content during the time the message was being carried from one place to another. In the modern era, cryptography has grown from basic message... Keep Reading »
All Computer Science Articles (by date) |