Cracking the Digital Vault: A Study of Cyber Espionage
By
2012, Vol. 4 No. 04 | pg. 1/3 | »
IN THIS ARTICLE
KEYWORDS
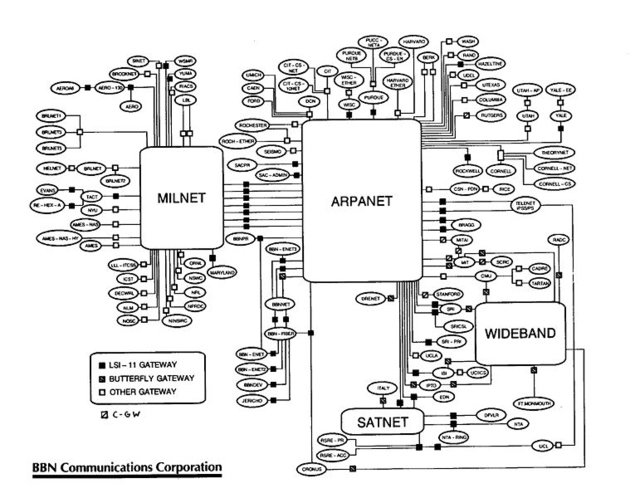
Today, we live in the aftermath of the Internet revolution. Humanity has never before been more interconnected or had as much access to the same tools and information. As a driving force behind globalization and modern progress, the Internet enables instant communication and access to information while providing a new medium for cultural exchange. But the Internet also presents new risks that do not recognize the conventional power structure. The usefulness of information technology (IT) for espionage cannot be ignored. After all, all warfare is based on deception.2 This paper examines how IT has changed the practices of espionage among states; it analyzeshow the availability of new technology makes it possible for corporations and private citizens to steal information and intellectual property from governments and each other; and finally, the paper concludes with an overview of the security situation as it currently stands and provides suggestions as to what can be done to improve it. The Birth of the InternetThe Internet originated with research funding provided by the Department of Defense Advanced Research Projects Agency (DARPA) to establish a military network. As its use expanded, a civilian segment evolved with support from the National Science Foundation (NSF) and other science agencies.3 While wired connections between mainframes at certain bases existed as early as the late 1950s,4 these rudimentary links had very limited functionality. The connection was usually unreliable, and in some cases could only transmit small bundles of data in one direction. While it is true that these connections paved the way for modern networking, in their earliest forms, these networks were little more than expensive telegraphs.One of the first networks (as we know them today) was AT&T's Switched Circuit Automatic Network designed for the US Army, which became AUTOVON in 1964.5 AUTOVON represented a technological leap forward, but was unable to address a fundamental problem with early networking, data delays caused by “queuing.” In the original network set up, data was transferred on a first-come-first-served basis and users found themselves waiting in virtual lines to transmit or receive information. As more users interacted across the network, the problem compounded and the wait-time at the back of the line got longer and longer. These delays would be potentially disastrous if a user needed to send data in an emergency, or if a commander were trying to gather real-time information from a battlefield. Fortunately, the answer came in the mid 60s through the work of Larry Roberts, an ARPA engineer, and Paul Baran, a DoD computer consultant.6 These men designed and implemented a system called packet-switching to solve the “queuing” conundrum. Packet switching is a digital networking communications method that groups all transmitted data into suitably-sized blocks, called packets. These packets are then individually sent across the network and reassembled by the target computer. When traversing network adapters, switches, routers and other network nodes, packets are buffered and reordered, resulting in variable delay depending on the amount of traffic in the network. While there still remained a delay in data transmission, packet switching networks did away with the long line and took individual packets from different users and sent them instead of completing one job at a time. Under heavy network traffic the processing and transmission speeds were slower than if single jobs were completed, but packet switching allowed for multiple simultaneous users to access the network and see their data transmitted without interruption. What was and is truly revolutionary about packet-switching is that the fundamental problem with data traffic was solved, and transmission speeds became a function of the networks themselves. With research and upgrades, our networks are growing constantly faster thanks to packet-switching. The firm Bolt Beraneck and Newman (BBN) designed the Interface Message Processor (IMP), which became the packet-switching node used to interconnect participant networks to the ARPANET from the late 1960s to 1989.7 It was the first generation of gateways, which are known today as routers. The first packets were successfully transmitted across ARPANet in 1969 and marked a true revolution in communication technology and the birth of the Internet as we know it today. The precursor to the Internet, ARPANet, was launched in 1968 as a network for Universities to share and collaborate on research and for the government and military to transmit and store data, but almost immediately took on a life of its own. Within a few months, it became apparent that the original host-to-host set up of the network, which required mainframes to literally dial into each other to communicate,8 would not be sufficient for the dynamic needs and growing demands of users. The second major revolution in communication technology came in 1970, barely two years after the launch of ARPANet, in the form of the Network Control Protocol (NCP). Initially, if any packets were lost, the protocol (and presumably any applications it supported) would come to a grinding halt. In this model NCP had no end-to-end host error control, since the ARPANET was to be the only network in existence and it would be so reliable that no error control would be required on the part of the hosts.9 In layman’s terms, NCP stabilized the original host-to-host connections but could not prevent crashes in the event of data error. This added stability allowed more computers to dial into each other simultaneously, increasing network usage and efficiency. NCP was used for thirteen years until the major change that occurs in 1983. The next communications revolution in the history of Internet development came in 1977 with the development of the Voiceover Internet Protocol (VoIP). As the name suggests, VoIP is used to transmit voice messages in real-time across the Internet and is what powers modern communication applications like Skype. Up to this point, the major objective of ARPA's Network Secure Communications (NSC) project had been to develop and demonstrate the feasibility of secure, high-quality, low-bandwidth, real-time, two-way digital voice communications over packet-switched computer communications networks.10 Given VoIP’s functionality and flexibility, it was highly desired by all levels of the military for its obvious command and control activities.11 VoIP is location independent; able to transmit multiple calls over a single broadband connection; and most importantly, it addresses most of the difficulties of creating a secure telephone connection over traditional phone lines.12 ARPA's NSC project supplied digitized speech secured by existing encryption devices and was quickly adopted into military communication systems in the following years.13 Finally we come to 1983, which brings with it the birth of the modern Internet. Up to this point, the military sphere of the Internet had existed in the same space as the research and civilian spheres. In response to an overload of traffic on the ARPANET, the Department of Defense split off the operation of its military traffic into a separate network called MILNET. The two networks collectively formed what was referred to as the 'Internet.14 The move was also motivated by security concerns. If problems developed on the ARPANET, the MILNET could be disconnected from it quickly by unplugging the small number of gateways that connected them. In fact, these gateways were designed to limit the interactions between the two networks to the exchange of electronic mail, a further safety feature.15 After the split, the Internet appeared as follows (circa 1985):
This split came at the same time as the transition from NCP to the new Transmission Control Protocol / Internet Protocol (TCP/IP). The ARPANet had migrated to the NCP network protocol in 1970; however, this protocol did have its limitations. It assumed end-to-end connectivity between the communicating hosts and did not handle interconnecting different networks well. It also did not tolerate packet loss, coming to a halt if a packet was lost. Bob Kahn and Vint Cerf had designed TCP/IP to overcome these limitations and permit interconnectivity between different networks and resend missing packets as necessary without crashing.16 17 With the new TCP/IP system in place, the Internet adopted the Internet Protocol version 4 (IPv4), believing that this would provide an inexhaustible number of addresses for servers and websites.18 TCP/IP was successfully used in 1977 to link together four networks, and IPv4 is still the platform used today across the Internet nearly twenty years later. Today, as the inexhaustible supply of addresses nears exhaustion, the Internet is once again migrating with the adoption of IPv6, which, as of 2011, is still in its infancy. Given the Internet’s ubiquity and functionality, I found it necessary to expand on a brief history of its development. Every advancement in communication and data transmission used in military networks is directly related to the research surrounding the technological development of the Internet. Also, as a tool, the Internet has unquestionably changed our way of life. Looking at a graph of Internet usage, one can see that as more connections are made and more users join for the first time, the Internet is growing exponentially. As the Internet becomes more prevalent, further research will lead to new technological breakthroughs, and networks all around the world will benefit.Continued on Next Page » Suggested Reading from Inquiries Journal
Inquiries Journal provides undergraduate and graduate students around the world a platform for the wide dissemination of academic work over a range of core disciplines. Representing the work of students from hundreds of institutions around the globe, Inquiries Journal's large database of academic articles is completely free. Learn more | Blog | Submit Latest in Computer Science |