|
From Interstate - Journal of International Affairs VOL. 2015/2016 NO. 2 The Internet as a Slippery Object of State Security: The Problem of Physical Border Insensitivity, Anonymity and Global Interconnectedness
By Memphis Krickeberg
Interstate - Journal of International Affairs
2016, Vol. 2015/2016 No. 2 | pg. 2/2 | «
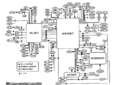
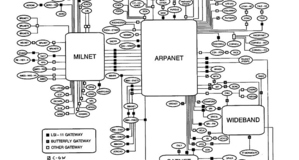
Cybersecurity narratives rest on a potentially deterritorialized and undetermined threat figure which equally menaces a wide array of referentobjects. It therefore appears to destabilize deep-rooted knowledge on what state security should be about in the realm of international relations. Moreover, it undermines the state's capacity of providing credible threat figures emanating from a "menacing outside" to its own populations. At the same time as cybersecurity discourses struggle to emphasize particular threat figures, incarnated by enemy states or terrorists, in a credible manner, the focus of security increasingly shifts to technical vulnerabilities which compromise flux circulation and associated risk calculations.
However, while cybersecurity discourses tend to present the reconceptualizing of state security studied above as an outcome of increased computer-interconnectedness, we would like to point out that these discourses are inscribed in a semantic field which has rendered a traditional, realist-type notion of state-security heavily ignored over, at least, the past thirty years. Further critical research should demonstrate how cybersecurity practices and discourses do not generate but merely amplify the dedifferentiation of security domains and the reference to a "continuum of threats" narrative which has characterized the development of international security since the 1980s.28 Stressing the historical continuity between these securitarian evolutions and cybersecurity would be a welcome step towards countering national and transnational discourses which use the so-called "novelty" of cyber-threats to further (in) securitize the Internet and dismantle/restructure its open character.
Achiary, A. Auverlot, D. Hamelin, J. ‘Cybersécurité, l'urgence d'agir', Centre d'Analyse Stratégique, Analysis note 324 (2013).
Aron, R. Paix et guerre entre les nations (Paris, Calman-Lévy, 2004).
Arquilla, J. ‘Cyberwar is already among us. But can it be controlled?', Foreign Affairs, 91:2 (2012).
Bockel, J, M. ‘Jean-Marie Bockel salue les dispositions du nouveau Livre Blanc en matière de cyberdéfense', Jean-Marie Bockel [Blog] 30 April 2013, Available at: http://jeanmariebockel.fr/jean-marie-bockel-salue-lesdispositionsdu-nouveau-livre-blanc-en-matiere-de-cyberdefense
Campbell, D. Writing Security: United Sates Foreign Policy and the Politics of Identity (Minneapolis, University of Minnesota Press, 1998).
Carr, M. The Irony of the Information Age: US Power and the Internet in International Relations, Doctoral Thesis (Canberra, Australian National University, 2011).
C.A.S.E. Collective, ‘Critical Approaches to Security in Europe: A Networked Manifesto', Security Dialogue, 37:4 (2006) pp. 443-487.
Chabaud, F. Recherche et développement en sécurité des systèmes d'information : orientations et enjeux, (Paris, Direction centrale de la sécurité des systèmes d'informations, 2008).
Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) pp.15-32.
Denning, D. ‘Cyber Security as an Emergent Infrastructure', in Security Education and Critical Infrastructures, edited by Armstrong, H. Irvine, Cynthia (New York, Kluwer Academic Publishers 2003) pp.1-2
Department of Homeland Security, Cyberspace Policy Review. Assuring a Trusted and Resilient Information and Communications Infrastructure (Washington, Office of the United States Department of Homeland Security, 2009).
Foucault, M. Sécurité, Territoire, Population: Cours au Collège de France, 1977-1978, (Paris, Seuil, 2004).
Foucault, M. Security, Territory, Population: Lectures at the Collège de France, (Hampshire, Palgrave MacMillan, 2009).
Hansen, L & Nissenbaum H. ‘Digital Disaster, Cyber Security, and the Copenhagen School', International Studies Quarterly, 53 (2009) pp. 1155– 1175.
Huysmans, J. ‘Security! What Do You Mean? From Concept to Thick Signifier', European Journal of International Relations, 4:2 (1998) pp. 226–255.
Labrie, M. La sécurisation du cyberterrorisme aux Etats-Unis Thèse de maîtrise (Montreal, Université du Québec à Montréal, 2011).
Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009).
Ministry of Defence. French White Paper. Defense and National Security, (Paris, Office of the Ministry of Defence of the French Republic, 2013).
Nye, J. The future of power, (Philadelphia, Public Affairs, 2011).
Paganini, P. ‘The business of censorship. Golden Shield Project, but not only ...' Security Affairs, [Blog] 19 November 2011, Available at: http://securityaffairs.co/wordpress/204/cyber-crime/business-ofcensorshipgolden-shield-project-but-not-only.html
Ryan, J. A history of the Internet and the digital future, (London, Reaktion Books, 2010).
Wamala, F. ITU National Cybersecurity Strategy Guide (Geneva, International Telecommunications Union, 2011).
- See: Denning, D. ‘Cyber Security as an Emergent Infrastructure', in Security Education and Critical Infrastructures, edited by Armstrong, H. Irvine, Cynthia (New York, Kluwer Academic Publishers 2003) pp.1-2; Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009); Department of Homeland Security, Cyberspace Policy Review. Assuring a Trusted and Resilient Information and Communications Infrastructure (Washington, Office of the United States Department of Homeland Security, 2009); Achiary, A. Auverlot, D. Hamelin, J. ‘Cybersécurité, l'urgence d'agir', Centre d'Analyse Stratégique, Analysis note 324 (2013).
- Foucault, M. Sécurité, Territoire, Population: Cours au Collège de France, 1977-1978, (Paris, Seuil, 2004).
- Chabaud, F. Recherche et développement en sécurité des systèmes d'information : orientations et enjeux, (Paris, Direction centrale de la sécurité des systèmes d'informations, 2008) p.4.
- Chabaud, F. Recherche et développement. p.4
- Chabaud, F. Recherche et développement. p.7
- See: Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009); Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) pp.15-32; Chapter 5 "Diffusion and Cyberpower" Nye, J. The future of power, (Philadelphia, Public Affairs, 2011).
- Campbell, D. Writing Security: United Sates Foreign Policy and the Politics of Identity (Minneapolis, University of Minnesota Press, 1998).
- Huysmans, J. ‘Security! What Do You Mean? From Concept to Thick Signifier', European Journal of International Relations, 4:2 (1998) pp. 226–255.
- Huysmans, J. Security!
- Huysmans, J. Security!
- Huysmans, J. Security!
- See: Hansen, L & Nissenbaum H. ‘Digital Disaster, Cyber Security, and the Copenhagen School', International Studies Quarterly, 53 (2009) pp. 1155–1175; Labrie, M. La sécurisation du cyberterrorisme aux Etats-Unis Thèse de maîtrise (Montreal, Université du Québec à Montréal, 2011).
- Carr, M. The Irony of the Information Age: US Power and the Internet in International Relations, Doctoral Thesis (Canberra, Australian National University, 2011). p.64
- Hansen, L & Nissenbaum H. Digital Disaster. p.1161
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Wamala, F. ITU National Cybersecurity Strategy Guide (Geneva, International Telecommunications Union, 2011). pp.48-49
- Ministry of Defence. French White Paper. Defense and National Security, (Paris, Office of the Ministry of Defence of the French Republic, 2013). p.100
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Aron, R. Paix et guerre entre les nations (Paris, Calman-Lévy, 2004).
- Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) p.15.
- Deibert, R. Risking Security. p.15 Wamala, F. ITU Cybersecurity
- Paganini, P. ‘The business of censorship. Golden Shield Project, but not only ...' Security Affairs, [Blog] 19 November 2011, Available at: http://securityaffairs.co/wordpress/204/cybercrime/ business-of-censorship-golden-shield-project-but-not-only.html
- Bockel, J, M. ‘Jean-Marie Bockel salue les dispositions du nouveau Livre Blanc en matière de cyberdéfense', Jean-Marie Bockel [Blog] 30 April 2013, Available at: http://jeanmariebockel.fr/jean-marie-bockel-salue-les-dispositions-du-nouveau-livre-blanc-enmatierede-cyberdefense
- This sovereignist view of security traditionally formulated by state elites and realists has of course never adequately reflected the effectivity of modern security logics. Indeed, Foucault has shown that security cannot be reduced to territorial defense but is to be envisaged as the counterpart and condition of possibility of modern governmentality i.e. the particular logic of power that emerged in the 18th century and which "has the population as its target, political economy as its major form of knowledge, and apparatuses of security as its essential technical instrument". Foucault, M. Security, Territory, Population: Lectures at the Collège de France, (Hampshire, Palgrave MacMillan, 2009). p.144
- Ryan, J. A history of the Internet and the digital future, (London, Reaktion Books, 2010).
- Wamala, F. ITU Cybersecurity.
- C.A.S.E. Collective, ‘Critical Approaches to Security in Europe: A Networked Manifesto', Security Dialogue, 37:4 (2006) pp. 443-487.
Achiary, A. Auverlot, D. Hamelin, J. ‘Cybersécurité, l'urgence d'agir', Centre d'Analyse Stratégique, Analysis note 324 (2013).
Aron, R. Paix et guerre entre les nations (Paris, Calman-Lévy, 2004).
Arquilla, J. ‘Cyberwar is already among us. But can it be controlled?', Foreign Affairs, 91:2 (2012).
Bockel, J, M. ‘Jean-Marie Bockel salue les dispositions du nouveau Livre Blanc en matière de cyberdéfense', Jean-Marie Bockel [Blog] 30 April 2013, Available at: http://jeanmariebockel.fr/jean-marie-bockel-salue-lesdispositionsdu-nouveau-livre-blanc-en-matiere-de-cyberdefense
Campbell, D. Writing Security: United Sates Foreign Policy and the Politics of Identity (Minneapolis, University of Minnesota Press, 1998).
Carr, M. The Irony of the Information Age: US Power and the Internet in International Relations, Doctoral Thesis (Canberra, Australian National University, 2011).
C.A.S.E. Collective, ‘Critical Approaches to Security in Europe: A Networked Manifesto', Security Dialogue, 37:4 (2006) pp. 443-487.
Chabaud, F. Recherche et développement en sécurité des systèmes d'information : orientations et enjeux, (Paris, Direction centrale de la sécurité des systèmes d'informations, 2008).
Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) pp.15-32.
Denning, D. ‘Cyber Security as an Emergent Infrastructure', in Security Education and Critical Infrastructures, edited by Armstrong, H. Irvine, Cynthia (New York, Kluwer Academic Publishers 2003) pp.1-2
Department of Homeland Security, Cyberspace Policy Review. Assuring a Trusted and Resilient Information and Communications Infrastructure (Washington, Office of the United States Department of Homeland Security, 2009).
Foucault, M. Sécurité, Territoire, Population: Cours au Collège de France, 1977-1978, (Paris, Seuil, 2004).
Foucault, M. Security, Territory, Population: Lectures at the Collège de France, (Hampshire, Palgrave MacMillan, 2009).
Hansen, L & Nissenbaum H. ‘Digital Disaster, Cyber Security, and the Copenhagen School', International Studies Quarterly, 53 (2009) pp. 1155– 1175.
Huysmans, J. ‘Security! What Do You Mean? From Concept to Thick Signifier', European Journal of International Relations, 4:2 (1998) pp. 226–255.
Labrie, M. La sécurisation du cyberterrorisme aux Etats-Unis Thèse de maîtrise (Montreal, Université du Québec à Montréal, 2011).
Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009).
Ministry of Defence. French White Paper. Defense and National Security, (Paris, Office of the Ministry of Defence of the French Republic, 2013).
Nye, J. The future of power, (Philadelphia, Public Affairs, 2011).
Paganini, P. ‘The business of censorship. Golden Shield Project, but not only ...' Security Affairs, [Blog] 19 November 2011, Available at: http://securityaffairs.co/wordpress/204/cyber-crime/business-ofcensorshipgolden-shield-project-but-not-only.html
Ryan, J. A history of the Internet and the digital future, (London, Reaktion Books, 2010).
Wamala, F. ITU National Cybersecurity Strategy Guide (Geneva, International Telecommunications Union, 2011).
Endnotes
- See: Denning, D. ‘Cyber Security as an Emergent Infrastructure', in Security Education and Critical Infrastructures, edited by Armstrong, H. Irvine, Cynthia (New York, Kluwer Academic Publishers 2003) pp.1-2; Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009); Department of Homeland Security, Cyberspace Policy Review. Assuring a Trusted and Resilient Information and Communications Infrastructure (Washington, Office of the United States Department of Homeland Security, 2009); Achiary, A. Auverlot, D. Hamelin, J. ‘Cybersécurité, l'urgence d'agir', Centre d'Analyse Stratégique, Analysis note 324 (2013).
- Foucault, M. Sécurité, Territoire, Population: Cours au Collège de France, 1977-1978, (Paris, Seuil, 2004).
- Chabaud, F. Recherche et développement en sécurité des systèmes d'information : orientations et enjeux, (Paris, Direction centrale de la sécurité des systèmes d'informations, 2008) p.4.
- Chabaud, F. Recherche et développement. p.4
- Chabaud, F. Recherche et développement. p.7
- See: Libicki, M. Cyberdeterrence and cyberwar, (Santa Monica, Rand Corporation, 2009); Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) pp.15-32; Chapter 5 "Diffusion and Cyberpower" Nye, J. The future of power, (Philadelphia, Public Affairs, 2011).
- Campbell, D. Writing Security: United Sates Foreign Policy and the Politics of Identity (Minneapolis, University of Minnesota Press, 1998).
- Huysmans, J. ‘Security! What Do You Mean? From Concept to Thick Signifier', European Journal of International Relations, 4:2 (1998) pp. 226–255.
- Huysmans, J. Security!
- Huysmans, J. Security!
- Huysmans, J. Security!
- See: Hansen, L & Nissenbaum H. ‘Digital Disaster, Cyber Security, and the Copenhagen School', International Studies Quarterly, 53 (2009) pp. 1155–1175; Labrie, M. La sécurisation du cyberterrorisme aux Etats-Unis Thèse de maîtrise (Montreal, Université du Québec à Montréal, 2011).
- Carr, M. The Irony of the Information Age: US Power and the Internet in International Relations, Doctoral Thesis (Canberra, Australian National University, 2011). p.64
- Hansen, L & Nissenbaum H. Digital Disaster. p.1161
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Wamala, F. ITU National Cybersecurity Strategy Guide (Geneva, International Telecommunications Union, 2011). pp.48-49
- Ministry of Defence. French White Paper. Defense and National Security, (Paris, Office of the Ministry of Defence of the French Republic, 2013). p.100
- Hansen, L & Nissenbaum H. Digital Disaster. p.1162
- Aron, R. Paix et guerre entre les nations (Paris, Calman-Lévy, 2004).
- Deibert, R. 'Risking Security: Policies and Paradoxes of Cyberspace Security', International Political Sociology, 4 (2010) p.15.
- Deibert, R. Risking Security. p.15 Wamala, F. ITU Cybersecurity
- Paganini, P. ‘The business of censorship. Golden Shield Project, but not only ...' Security Affairs, [Blog] 19 November 2011, Available at: http://securityaffairs.co/wordpress/204/cybercrime/ business-of-censorship-golden-shield-project-but-not-only.html
- Bockel, J, M. ‘Jean-Marie Bockel salue les dispositions du nouveau Livre Blanc en matière de cyberdéfense', Jean-Marie Bockel [Blog] 30 April 2013, Available at: http://jeanmariebockel.fr/jean-marie-bockel-salue-les-dispositions-du-nouveau-livre-blanc-enmatierede-cyberdefense
- This sovereignist view of security traditionally formulated by state elites and realists has of course never adequately reflected the effectivity of modern security logics. Indeed, Foucault has shown that security cannot be reduced to territorial defense but is to be envisaged as the counterpart and condition of possibility of modern governmentality i.e. the particular logic of power that emerged in the 18th century and which "has the population as its target, political economy as its major form of knowledge, and apparatuses of security as its essential technical instrument". Foucault, M. Security, Territory, Population: Lectures at the Collège de France, (Hampshire, Palgrave MacMillan, 2009). p.144
- Ryan, J. A history of the Internet and the digital future, (London, Reaktion Books, 2010).
- Wamala, F. ITU Cybersecurity.
- C.A.S.E. Collective, ‘Critical Approaches to Security in Europe: A Networked Manifesto', Security Dialogue, 37:4 (2006) pp. 443-487.
Save Citation » (Works with EndNote, ProCite, & Reference Manager)
APA 6th
Krickeberg, M. (2016). "The Internet as a Slippery Object of State Security: The Problem of Physical Border Insensitivity, Anonymity and Global Interconnectedness." Interstate - Journal of International Affairs, 2015/2016(2). Retrieved from http://www.inquiriesjournal.com/a?id=1344
MLA
Krickeberg, Memphis. "The Internet as a Slippery Object of State Security: The Problem of Physical Border Insensitivity, Anonymity and Global Interconnectedness." Interstate - Journal of International Affairs 2015/2016.2 (2016). <http://www.inquiriesjournal.com/a?id=1344>
Chicago 16th
Krickeberg, Memphis. 2016. The Internet as a Slippery Object of State Security: The Problem of Physical Border Insensitivity, Anonymity and Global Interconnectedness. Interstate - Journal of International Affairs 2015/2016 (2), http://www.inquiriesjournal.com/a?id=1344
Harvard
KRICKEBERG, M. 2016. The Internet as a Slippery Object of State Security: The Problem of Physical Border Insensitivity, Anonymity and Global Interconnectedness. Interstate - Journal of International Affairs [Online], 2015/2016. Available: http://www.inquiriesjournal.com/a?id=1344
Suggested Reading from Inquiries Journal
Today, we live in the aftermath of the Internet revolution. Humanity has never before been more interconnected or had as much access to the same tools and information. As a driving force behind globalization and modern progress, the Internet enables instant communication and access to information while providing a new medium for... MORE»
Cyber security is a compelling problem for scholars of International Politics. Internet technology is so thoroughly integrated into civil society, commerce, governance, critical infrastructures, intelligence collection and law enforcement that the stakeholders necessary to cyber security practices and policies are diverse and complex... MORE»
In Cyber War Will Not Take Place1, Thomas Rid develops his argument on the concept of "cyberwar", previously formulated in an article of the same name2 published in January 2012. His chief point is that "cyber war has never happened in the past, it does not occur in the present, and it is unlikely that it will disturb... MORE»
There is a widespread belief that as societies and governments become increasingly reliant upon information technology, they in turn are becoming more vulnerable to a whole range of cyber-threats.1 Whether these dangers are capable of generating enough damage to warrant a redistribution of government resources is the question at the heart of this essay. This paper provides an evaluation of the cyber-threat arguing that it deserves recognition as... MORE»
Latest in International Affairs
2022, Vol. 14 No. 04
With over 10 million stateless people globally, statelessness has increasingly become a pressing issue in international law. The production of statelessness occurs across multiple lines including technical loopholes, state succession, and discriminatory... Read Article »
2021, Vol. 13 No. 09
The COVID-19 crisis has exacerbated current global challenges. However, this article argues that this time of crisis can also be a unique opportunity for the existing global economic institutions - G20, WTO, IMF, and World Bank (WB) - to make the... Read Article »
2021, Vol. 13 No. 02
On January 1st, 1959, a small band of Cuban rebels shocked the world, overthrowing the American-backed dictator Fulgencio Batista. These rebels were especially known for their guerrilla tactics and their leaders, such as Fidel Castro and Ernesto... Read Article »
2021, Vol. 13 No. 01
Israel has increased the nation’s security presence around the Gaza Strip and in the West Bank. Here, the research project analyzes how transaction costs resulting from Israeli security policy impact the output of manufacturing activities... Read Article »
2020, Vol. 12 No. 09
The necessity of international relief is unending as new crises continue to emerge across the world. International aid plays a crucial role in shaping how affected communities rebuild after a crisis. However, humanitarian aid often results in a... Read Article »
2019, Vol. 11 No. 10
This article aims to present the biopiracy of traditional knowledge from India by the United States, which has occurred directly through the use of patent law and indirectly through economic power and cultural imperialism. Throughout this essay,... Read Article »
2018, Vol. 10 No. 10
After joining the European Union (EU) and the North Atlantic Treaty Organization (NATO) in 2004, Estonians felt secure and in charge of their future. However, following the 2007 Bronze Horseman incident in the Estonian capital of Tallinn which included... Read Article »
|