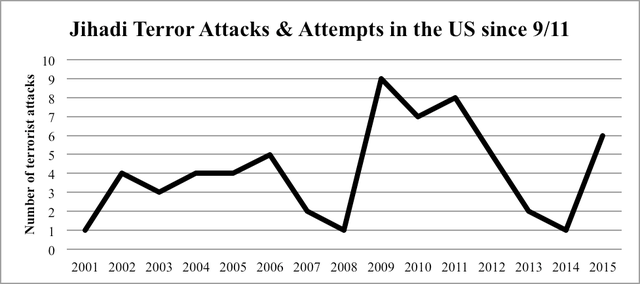
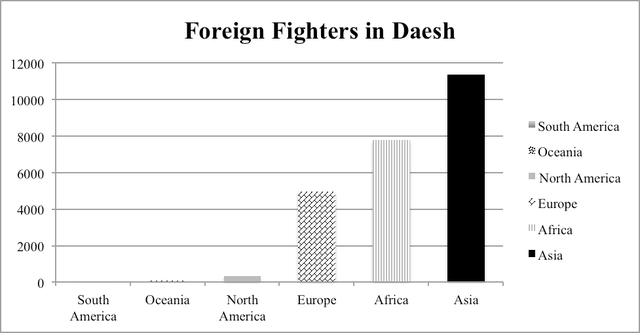
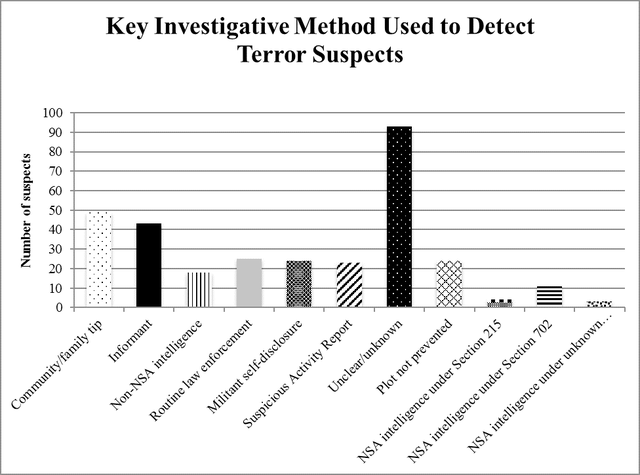
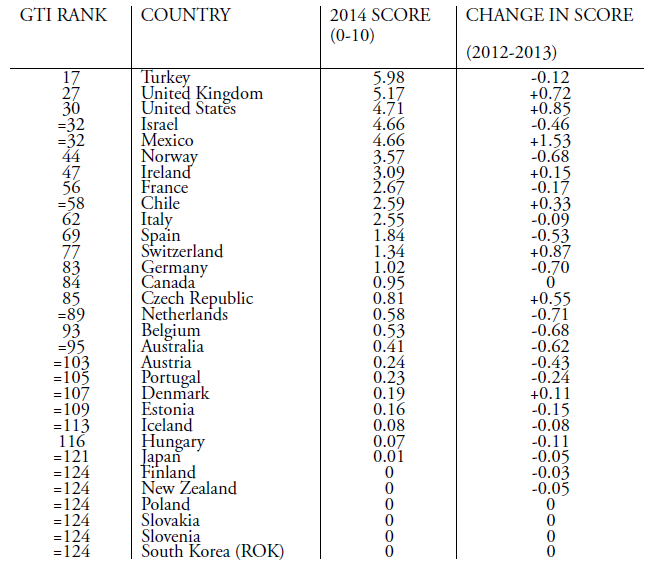
From Cornell International Affairs Review VOL. 9 NO. 2Hearts and Minds: A Comparison of Counter-Radicalization Strategies in Britain and the United StatesMethodologyFirst, I will use four case studies to study whether the strategy has been successful or not. Each strategy will have one "success" and one "failure" case study. The first metric is numeric. While complete statistics are unavailable due to the clandestine nature of most national security operations, there are a number of sources that track radicalization instances since 9/11.33 I will provide quantitative data outlining the general success of law enforcement in preventing radicalization or terrorist plots when it is available. The second metric is success. A criterion for a successful counter-radicalization strategy should take into consideration criticisms of counter-radicalization programs. It should prevent terrorist activity while not causing further sociopolitical marginalization of the Muslim community in the country (see the "Extant literature" section). The case studies should illuminate in what ways the strategy succeeds, and in what areas it fails. The second criterion is that it should address the root concerns of homegrown terrorism in Western states, namely political marginalization. The third metric is time. The study will be bounded from 2011 to the end of 2015, when this paper was first written. As previously described in the formation of the CVE and Prevent strategies above, both strategies were implemented in 2011. Hence, case studies that take place before the implementation of these strategies are irrelevant; this study only uses case studies that take place after the counter-radicalization strategies are implemented to examine the hypotheses. Nevertheless, this study integrates statistics from before the implementation of the counter-radicalization strategies in order to show relevant longer-term terrorism and radicalization trends that may not be immediately apparent when examining a four-year time period. Methodological difficultiesFor most Americans, homegrown terrorism and radicalization has never been as major a concern as terrorism abroad. The reason is clear, as the number of attempted terror attacks in the United States never number more than ten per year. Out of all the incidents described above, only five succeeded,34 resulting in thirty-four casualties total.35 The rest ended in arrest and law enforcement intervention. Attacks dating back to 2001 are shown below in order to depict the unusually high level of jihadist terrorist activity from 2009 to 2011. Moreover, this graph does not show the numbers of Americans going abroad to serve as foreign fighters for Daesh; in late October, the FBI detained nearly seventy people who had alleged connections to Daesh.36 Two conclusions can be drawn from these data. First, this paper does not include radicals who go abroad to fight for Daesh and other jihadist groups, although they construe a major part of the modern terrorist threat to Western states. Second, this explains the lack of data regarding counter-terrorism and counter-radicalization in Western states in prior years, as a majority of scholarly attention was focused on terrorism in the Middle Eastern region throughout the 2000s. Moreover, even though the UK and the US suffer the second and third highest rates of terrorism among OECD countries (see Appendix A), it is important to note that the United States does not face the same threat from radicalization that its European allies face. By August 2015, an estimated 350 Daesh foreign fighters originate from the United States and Canada combined. Meanwhile, over 700 foreign fighters are from the United Kingdom alone. The UK ranks among the world's top ten countries from which foreign fighters originate; among European countries, only Russia and France outrank it.38 As such, radicalization is a much more immediate concern to the British than to the Americans. The case studies cannot be separated from the environmental and political contexts in which they took place. Thirdly, this study is limited in the sense that counter-radicalization is inherently difficult to measure: its successes is defined by its absences, not its incidents. As explained by Vidino, a successful counter-radicalization strategy can only be measured by the number of people who would have gone on to commit terrorist attacks but opted not to or were stopped by authorities due to the counterradicalization strategy.40 The latter is measurable, the former nearly impossible. Moreover, Lorenzo also raises a serious quandary about assessing failure: "If, for example, one hundred individuals go through a deradicalization program and only a handful of them revert to terrorism, how is the program to be assessed?"41 Those questions are difficult to answer and far beyond the purview of this paper. Hence, this study will use the metrics described above, but they are in no way comprehensive metrics of success. Successessful Prevention EffortsPipe bombs in ManhattanNoted terrorism scholar John Mueller published a book of case studies of US radicalization since 9/11.42 Out of sixty-one documented cases, twenty take place after 2011. Most of these cases end in arrest, either by local law enforcement or the FBI. One such case is that of Jose Pimentel. Pimentel started reading the Qu'ran in 2001, and converted to Islam in 2004. In 2010, following divorce and personal failure, he was worrying relatives with his increasing obsession with Islam. Around that time, he started to post online about his radical beliefs, praising Osama bin Laden for perpetrating the 9/11 attacks. By this time, law enforcement had been tailing Pimentel for over two years. Initially, Schenectady police tipped the NYPD off when Pimentel moved to New York City, because Pimentel had expressed a desire to undergo terrorist training in Yemen. NYPD informants later befriended Pimentel and accompanied him as he purchased materials for his pipe bombs. On 19 November 2011, Pimentel was arrested by the NYPD after being videotaped making pipe bombs, which he intended to send to American military personnel returning from abroad. The timing of the plot came soon after Anwar al-Awlaki, an American radical Islamic cleric hiding in Yemen, was killed by drone strike.43 It is suspected that he was so easily caught because of the freeness with which he would discuss his radical opinions, especially online. The NYPD is considered to be the most prepared in the nation regarding possible terrorist attacks. Police departments across the nation emulate their tactics, especially the use of agent provocateurs, in detecting and preventing homegrown terrorism.44 Bristol's failed suicide bomberAndrew Ibrahim frequently smoked marijuana, spent the vast majority of his time on Internet games, got expelled from a series of private schools, and frequently researched Osama bin Laden and explosives on his father's computer while growing up. After drug abuse, he failed out of his college courses, and experienced numerous other personal failures. By this time in 2007, he had found Islam and converted, changing his name to Isa; he started to wear the traditional white robes, headscarf, and sandals. He briefly returned to drugs and studying for his A-levels as he was more interested in the politics than the religion, but quickly became obsessed with suicide bombers and the ongoing war in Iraq.45 After failing his exams in early spring 2008, he started to purchase suicide bomb equipment. He then researched the history and the process of making a suicide bomb vest. On 16 April 2008, his suspicious activities were reported to the police. They quickly arrested him and removed the explosives from his council flat in Bristol.46 AnalysisThe CVE strategy has been considered a success in apprehending and preventing dozens of would-be terrorists via the use of agent provocateurs, so the strategy remains in place. That Pimentel was noticed and followed by the NYPD the moment he returned to New York shows careful observation, and the fact that he was arrested the moment he entered the hardware store to purchase bomb supplies is evidence of law enforcement assiduousness in taking reported threats seriously and moving to prevent violence effectively. Speaking more broadly, what is noticeable about Mueller's documented case studies is just how few of them result in violence. In the wake of the San Bernadino attacks, it may not seem as if Americans are safe from terrorists armed with guns. However, out of sixty-two incidents, only five failed to be caught by police or the FBI (see Appendix B). Americans are more likely to hear about the terrorist attacks that do occur instead of the plots that failed, but the evidence shows just how assiduous law enforcement is in monitoring individuals with radical tendencies. Pimentel's case study is the most typical instance of homegrown terrorism in the US. Out of 317 jihadist suspects since 9/11, 182 of them were foiled by traditional investigative measures. Traditional investigative measures include six categories: community/family tip, informant, non-NSA intelligence (provided by the CIA, FBI, etc.), routine law enforcement, militant self-disclosure, and Suspicious Activity Reports. Pimentel's case study falls underneath the routine law enforcement category, but it also has an element of militant self-disclosure, as Pimentel posted his sentiments online prior to his arrest. Pimentel's case study exposes how little the CVE strategy relies on signals intelligence (SIGINT), the kind of intelligence popularized by public perceptions of the NSA. NSA data collection counts for very few case studies; to be exact, only eighteen of the 317 suspects were caught via SIGINT. The vast majority of domestic terror suspects are detected through traditional human intelligence (HUMINT) methods. HUMINT typically uses informants and agent provocateurs to collect enough evidence to indict suspects.48 This has raised a great level of controversy among Americans, because nonviolent radicals may be incited to do something illegal via an agent provocateur's goading. It sounds eerily like the plot of 1984, which is enough to scare the majority of American citizens. However, it is worth noting the sheer number of Mueller's case studies that have been foiled; the vast majority of them were achieved via the use of agent provocateurs, so no one can deny that it actually succeeds in bringing out violent terrorists and preventing them from turning their violent deeds from aspirations into operations. Meanwhile, Ibrahim was identified via community tip by a number of people in Bristol's Muslim community who had attended a Prevent awareness workshop.49 As such, it shows the importance of raising awareness about radicalization and its threats to the public at large, especially Muslim communities. However, the case study still results in arrest, which belies the intention of Prevent being used to preempt police activity and prevent young Brits from being jailed. Nevertheless, the importance of community participation in preventing terrorism remains paramount, as civilians are far more likely to come into contact with a would-be terrorist than a law enforcement officer on duty. That the British have mobilized their public and promoted safety regarding radicalization is also commendable. In this case study, that awareness has saved countless lives. The Ibrahim and Pimentel case studies are quite similar. Both men were under thirty years of age and were not socialized in strict Muslim households. They lived in urban environments that promoted a sense of isolation being separated from society. They ran against social norms with their criminal activity, which moved them up the action radicalization pyramid. Pimental and Ibrahim both studied Islam and were part of the religion, enjoying the social structure that entered their lives, which moved them to the base of the opinion radicalization pyramid. The combination of the two made them incredibly vulnerable to the jihadist narrative; that narrative invited both men to become part of a special group who had been unfairly treated by society and whose situation was dire – they had to act or face extinction.50 Both men disengaged from the religious nature of Islam and gravitated towards the political events involving the Middle East, which is what made them shift to the apex of the opinion radicalization pyramid. Jocelyne Cesari describes the social shift: "The temporary loss of embeddedness [in the Tabligh, or the apolitical movement whose goal is to increase Muslim orthodoxy, commonly called the ‘Jehovah's Witnesses of Islam'] made these jihadis vulnerable to Salafi interpretations … It provides an alternative to the isolation and estrangement of an urban environment that caters to the affluent and culturally dominant citizen."51 Because both had lower thresholds to breaking the law due to prior criminal histories, it allowed both to bridge the gap between believing in jihadism and attempting it. However, an interesting twist emerges at the end of the Ibrahim case study. By the time authorities raided Ibrahim's flat, he had already purchased suicide bomb materials. For all of the case study similarities, Pimentel was arrested before he could complete purchasing suicide bomb materials. I argue that Ibrahim would have never completed the suicide bomb had this case taken place in the US. Prevent was less effective than CVE in terms of how quickly authorities were able to determine the existence of a national security threat in this case study comparison. Failed Prevention AttemptsTragedy in BostonTamerlan and Dzhokhar Tsarnaev are the two brothers who gained notoriety for carrying out the Boston Marathon Bombing. Tamerlan Tsarnaev, the elder brother, also experienced personal failure; during this time, Zubeidat encouraged him to turn to religion. In January 2012, Tamerlan visited Chechnya in order to renew his Russian passport; it is thought that he made contact with Chechen insurgents at this time. Meanwhile, the younger brother Dzhokhar admired his elder immensely, and became embedded in Tamerlan's increasing radicalism. The brothers originally plotted to bomb the Charles River area in Boston on July 4, but when incendiary devices proved easy to procure, they modified their plans. On 15 April 2013, the Tsarnaev brothers set off two improvised explosive devices (IEDs) at the Boston Marathon finish line, killing four and wounding over 200 people. They had originally planned to commit a suicide bombing in Times New Square with six other IEDs, but were intercepted by police.52 Tamerlan was killed in a police shootout and Dzhokhar was apprehended less than a day later. Two years later, he was sentenced to death in a jury trial.53 Not a surveillance state, but a suspicious oneIn this case study, names have not been released to the public. As such, each person will be designated with an initial in order to help identify the plethora of characters in this case study. A twelve year-old schoolboy ("A") was also reported to the Prevent authorities on suspicion of being radicalized. A was doing a home economics lesson, and the teacher ("B") had instructed his or her students to procure a chicken. At the time, there was a news story about halal slaughterhouses being shut down. A told his teacher that he would not be able to procure a halal chicken. When asked by B as to why, A responded, "It's because the government hates Muslims." B told the preteen's mother ("C"), who agreed to talk to her child. C said that she was careful about the material she showed her son. However, child services still rang a week later. Because A was being bullied at his school, he was frequently tardy. The tardiness, though, was attributed to praying at a mosque, not because he was reluctant to go to a school where he'd be bullied. Furthermore, C went on holiday and left A and his brother ("D") with her husband ("E"). A was ill during this time, and E called his school to excuse his absence. Since A and D did not attend the same school, A's school called D's school to check whether D was in class or not. A's school was under the presumption that C had taken her children off to the Middle East, presumably to join Daesh. This is but one case study among many reports of Muslim schoolchildren finding themselves being reported to Prevent authorities as a result of teachers being mandated to report any suspicious activity to Prevent.54 AnalysisMost noticeably, Tamerlan Tsarnaev had been placed in an FBI database following a notification from the Russian security services (FSB); however, after an interview, the FBI was unable to declare him an important enough threat to national security to warrant close observation. Later that year, the FSB warned the CIA of the threat that Tamerlan posed to US national security. Unlike the Pimentel case study, the Tsarnaev brothers did not post their beliefs or plans online, as the former did. Moreover, neither of the Tsarnaev brothers had any connection with al-Qaeda or any other radical group, although al-Qaeda's Inspire magazine was quick to claim responsibility for the attack. Law enforcement and intelligence agencies failed to detect the Tsarnaev brothers until it was too late for the first set of bombings, but acted quickly and effectively to prevent the second set of bombings.55 The Boston Marathon Bombing case study shows the limitations of relying so heavily upon HUMINT. Even though traditional surveillance methods have caught so many individuals, they failed to catch 7.6% of the perpetrators. SIGINT requires few personnel; the bulk of expenses are for sophisticated technology and equipment. By comparison, HUMINT requires several personnel to serve as agent provocateurs and analysts. Technology is still at the stage where a human can detect a terror plot better than a machine, but it is also a weakness because the US does not have the financial means and the time to investigate every suspected terrorist. Law enforcement individuals need to be lucky all the time, but terrorists need to be lucky just once in order to strike fear into the heart of a nation. Even though 1.3 million people die in car crashes annually, the fear and public discourse that goes into terrorism versus car crashes is much greater. By contrast, the effects of over-reporting are much less newsworthy as they do not cause casualties. There are noticeable consequences of mandating that teachers and other private citizens report suspicious activity to the government, but they are not detrimental to society in the short-term, as the Tsarnaev case study was. Nonetheless, in a socially and economically stratified society that results from centuries of a land-based aristocracy, the suspects for radicalization are inevitably from the Muslim minority subject to heightened scrutiny ever since the 7/7 tube bombings. That is not to say that people will impose certain Islamophobic biases upon their reporting of radicalization, but Homa Khaleeli's article makes it clear that no one has reported a young Caucasian student for white supremacist statements like those made by Anders Breivik, who shot and killed twenty-nine Oslo children in 2009.56 Those reported to Prevent are all Muslim schoolchildren with ethnic Arab backgrounds, one of them three years old. The title of the article reflects the fear the parents have: that the British government will take the children to properly instill "British values" into them. It reeks of targeted political repercussions instead of social cohesion. A large part of this phenomenon is that the Prevent strategy likens radicalization to other anti-social behavior and psychiatric issues akin to those exhibited by assassins and school shooters. While homegrown terrorists and school shooters do exhibit some similarities (as noted in "The theory of radicalism" section), stronger indications of radicalization are the inability to endure perceived hypocrisy and the personal connection with alleged victims, which allows homegrown extremists to connect with terrorists outside of an organized group. As such, the Prevent strategy may be telling its citizens to look for the wrong signs and to misinterpret them. The schoolchild in the halal chicken case study should have been referred to a counselor or psychologist, not counterterrorism authorities. There is a real problem in creating such a public and visible strategy with a simple moniker as Prevent. The word "prevent" alone has a massive range of interpretation. Among the general public, it might evoke a sense of "preventing violent extremism," but among English Defence League members, it might imply a legal pretext for bigotry. This is a group that promotes xenophobia as a matter of public policy. It explicitly labels radical ideas and statements as a problem, and this can result in overreaction when a citizen does not know the difference between depression and radicalization. The Prevent strategy chips away at civil society by mandating that citizens report on each other on the basis of suspicions, which targets Muslims in practice because of the larger sociopolitical context in which this policy takes place, exacerbated by the twenty-four-hour news cycle that brings fresh news of Daesh's barbaric tactics every day when the sun dawns. Every citizen, even Prevent-trained, will have a different education level when it comes to political science and counterterrorism studies and a different threshold of what constitute or does not constitute radicalization. By not taking into account citizens' political identity and upbringing, the British government implies that all citizens are treated equally in society, which is not true. The delay in a moderate Muslim countermovement, epitomized by Twitter hashtags such as #NotInMyName, has harmed the perception of Muslims in Western countries, which allows Islamophobic demagoguery to gain traction. By assuming that citizens are effectively unbiased and always able to discern between an actual case of radicalization and potential overreaction, the British government is in effect allowing citizens to act upon any implicit biases, which can lead to further political radicalization from Muslims who feel that they are being targeted by the government and non-Muslim Brits. Of course, with that being said, this is a society that created and popularized the #YouAintNoMuslimBruv hashtag, which was applauded by Prime Minister Cameron.57 Suffice to say that Islamophobia is not a popular sentiment in the UK as it is among presidential candidate Donald Trump's xenophobic supporters. With that being said, policies like Prevent that attempt to cull cognitive radicalization would likely lead to several problems in America. The questions raised by this comparison reveal the crux behind the debate as whether to focus on cognitive or behavioral radicalization. Should a country only focus on behavioral radicalization, its law enforcement capability may be limited by the influx of simultaneously monitoring many would-be terrorists, since there is no single path of radicalization. As evidenced by the three case studies of radicalization, all three connected to radical Islam via different methods: Internet, controversial political actions taken by the US, and connections with Chechen terrorists. This has been borne out by other studies as well, as noted by other scholars.58 This can result in another Boston Marathon Bombing again, where authorities may not be able to effectively detect a serious terror threat until it is too late. On the other hand, if one includes measures against cognitive radicalization from the outset, then it can potentially deter some of these threats, but at an additional cost of alienating a segment of the population that feels unfairly targeted. That resentment can incite violence, which is the opposite of its goal. Conversely, by including the First Amendment as priority in its counter-radicalization strategy, the American method is very clear and explicit about its goals. It does not brand the strategy with a simple moniker that can be misrepresented; it labels itself as countering violent extremism only, not permitting inadvertent bigotry, and separating itself from bigoted statements. The CVE strategy is much more downplayed and utilizes a number of existing frameworks rather than establishing a new program entirely. The White House justifies this by saying: "This reliance, however must not change the nature or purpose of existing relationships. In many instances, our partnerships and related activities were not created for national security purposes but nonetheless have an indirect impact on countering violent extremism (CVE)."59 It is careful to utilize existing law enforcement methods and frameworks so that it is not perceived as breaking the law in the name of national security but rather maintaining the law to defend Americans from what would already be considered illegal. It does, however, court controversy through its use of agent provocateurs and its use in inspiring a small cabal of citizens towards further radicalism instead of dissuading them from extremism. Nevertheless, its success cannot be understated in an era of increasing identity-driven divisions in the American political atmosphere.60Continued on Next Page » Suggested Reading from Inquiries Journal
Inquiries Journal provides undergraduate and graduate students around the world a platform for the wide dissemination of academic work over a range of core disciplines. Representing the work of students from hundreds of institutions around the globe, Inquiries Journal's large database of academic articles is completely free. Learn more | Blog | Submit Latest in Political Science |